实验目的:
1、掌握编号标准ACL的基本编写。
2、理解编号标准ACL的基本特性。
实验拓扑:
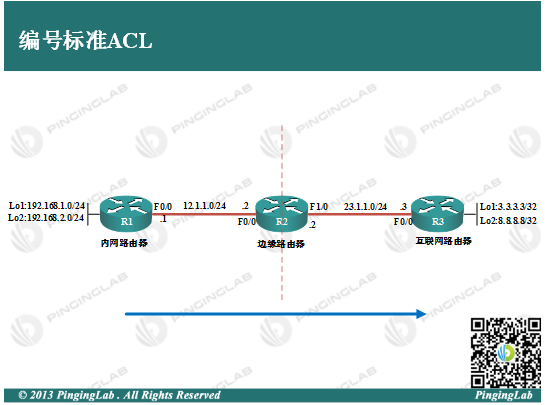
实验步骤:
1、依据图中拓扑,配置各个路由器的IP地址,并部署静态路由保证全网连通,配置如下:
R1上
R1(config)#ip route 23.1.1.0 255.255.255.0 12.1.1.2 R1(config)#ip route 3.3.3.3 255.255.255.255 12.1.1.2 R1(config)#ip route 8.8.8.8 255.255.255.255 12.1.1.2
R2上
R2(config)#ip route 192.168.1.0 255.255.255.0 12.1.1.1 R2(config)#ip route 192.168.2.0 255.255.255.0 12.1.1.1 R2(config)#ip route 3.3.3.3 255.255.255.255 23.1.1.3 R2(config)#ip route 8.8.8.8 255.255.255.255 23.1.1.3
R3上
R3(config)#ip route 12.1.1.0 255.255.255.0 23.1.1.2 R3(config)#ip route 192.168.1.0 255.255.255.0 23.1.1.2 R3(config)#ip route 192.168.2.0 255.255.255.0 23.1.1.2
测试连通性,如下:
R1#ping 3.3.3.3 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/40 ms R1#ping 8.8.8.8 source 192.168.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 36/43/56 ms
可以看到,内网与外网通信没有问题。
2、在R2上部署编号标准ACL,使得内网网段192.168.1.0/24不能访问外网,其他都能访问,配置如下:
R2(config)#access-list 1 deny 192.168.1.0 0.0.0.255 R2(config)#access-list 1 permit any R2(config)#int f0/0 R2(config-if)#ip access-group 1 in R2(config-if)#exit
测试ACL的效果,让内网路由器R1访问外网路由器R3,如下:
R1#ping 3.3.3.3 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 UUUUU Success rate is 0 percent (0/5) R1#ping 8.8.8.8 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 UUUUU Success rate is 0 percent (0/5) R1#ping 3.3.3.3 source 192.168.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 16/38/64 ms R1#ping 8.8.8.8 source 192.168.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 20/38/48 ms
从上面很明显的看出,内网网段192.168.1.0/24无法访问外网,其他网段可以。
3、在R2上部署编号标准ACL,使得IP地址192.168.2.1可以Telnet本地,而其他IP地址没法访问,实现安全管理,配置如下:
R2上
R2(config)#line vty 0 15 R2(config-line)#no login R2(config)#access-list 2 permit host 192.168.2.1 R2(config)#line vty 0 15 R2(config-line)#access-class 2 in
此时在R1和R3上Telnet R2,如下:
R1#telnet 12.1.1.2 Trying 12.1.1.2 ... % Connection refused by remote host R3#telnet 23.1.1.2 Trying 23.1.1.2 ... % Connection refused by remote host R1#telnet 12.1.1.2 /source-interface lo2 Trying 12.1.1.2 ... Open R2>
可以看到,只有192.168.2.1才能远程访问Telnet。编号标准ACL可以实现最基础的访问限制和安全管理,但是在限制要求比较高的情况下则无能为力,若上面的要求“192.168.1.0无法访问互联网”修改成“192.168.1.0无法访问3.3.3.3可以访问8.8.8.8”,则编号标准ACL无法实现,因为标准ACL只能匹配源,不能匹配目的以及具体的端口和协议。此实验完成。
- 还没有人评论,欢迎说说您的想法!
