实验目的:
1、掌握时间ACL的基本编写。
2、理解时间ACL的基本特性。
实验拓扑:
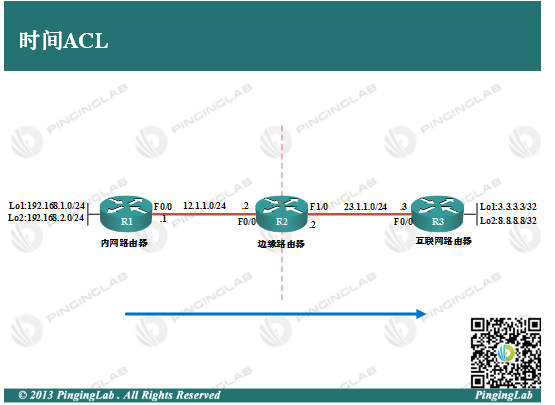
实验步骤:
1、依据图中拓扑,配置各个路由器的IP地址,并部署静态路由保证全网连通,配置如下:
R1上
R1(config)#ip route 23.1.1.0 255.255.255.0 12.1.1.2 R1(config)#ip route 3.3.3.3 255.255.255.255 12.1.1.2 R1(config)#ip route 8.8.8.8 255.255.255.255 12.1.1.2
R2上
R2(config)#ip route 192.168.1.0 255.255.255.0 12.1.1.1 R2(config)#ip route 192.168.2.0 255.255.255.0 12.1.1.1 R2(config)#ip route 3.3.3.3 255.255.255.255 23.1.1.3 R2(config)#ip route 8.8.8.8 255.255.255.255 23.1.1.3
R3上
R3(config)#ip route 12.1.1.0 255.255.255.0 23.1.1.2 R3(config)#ip route 192.168.1.0 255.255.255.0 23.1.1.2 R3(config)#ip route 192.168.2.0 255.255.255.0 23.1.1.2
测试连通性,如下:
R1#ping 3.3.3.3 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/40 ms R1#ping 8.8.8.8 source 192.168.2.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 192.168.2.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 36/43/56 ms
可以看到,内网与外网通信没有问题。
2、在R2上部署基于时间的ACL,使得内网网段192.168.1.0/24在工作日上班时间8:30到18:00不能够访问外网,配置如下:
①设备路由器本地时间
R2(config)#clock timezone BJ +8 R2#clock set 10:00:00 30 JULY 2013
②设备时间范围
R2(config)#time-range PL R2(config-time-range)#periodic weekdays 8:30 to 18:00
③设置ACL并调用时间范围
R2(config)#access-list 100 deny ip 192.168.1.0 0.0.0.255 any time-range PL R2(config)#access-list 100 permit ip any any
④接口下调用ACL
R2(config)#int f0/0 R2(config-if)#ip access-group 100 in
3、测试时间ACL。
查看时间范围
R2#show time-range time-range entry: PL (active) periodic weekdays 8:30 to 18:00
查看ACL状态
R2#show ip access-lists
Extended IP access list 100
10 deny ip 192.168.1.0 0.0.0.255 any time-range PL (active)
20 permit ip any any
让R1访问外网
R1#ping 8.8.8.8 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 UUUUU Success rate is 0 percent (0/5) R1#ping 3.3.3.3 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 UUUUU Success rate is 0 percent (0/5)
可以看到,在特定时间范围内,此时192.168.1.0网段无法访问外网。可以尝试将本地路由器的时间修改,如下:
修改本地时间
R2#clock set 22:00:00 30 JULY 2013
查看时间范围
R2#show time-range time-range entry: PL (inactive) periodic weekdays 8:30 to 18:00 used in: IP ACL entry
查看ACL状态
R2#show ip access-lists
Extended IP access list 100
10 deny ip 192.168.1.0 0.0.0.255 any time-range PL (inactive) (30 matches)
20 permit ip any any
让R1访问外网
R1#ping 8.8.8.8 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 48/60/64 ms R1#ping 3.3.3.3 source 192.168.1.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds: Packet sent with a source address of 192.168.1.1 !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 52/63/68 ms
可以看到,当不再特定的时间范围内,192.168.1.0/24能够访问外网。
从以上实验可以看到,时间ACL相比传统的ACL来说,加入了时间属性,使得流量管理更加弹性化。此实验完成。

1234